Earlier today we saw a blog post from our friends over at Sunbelt about a compromise of Bank of India's website .
Due to this compromise millions of Customers of the banks website were left in the hands of attackers from Russia, who managed to install a number of Trojans and root kits in the computers of the bank's innocent customers, who may be using the net banking facility.
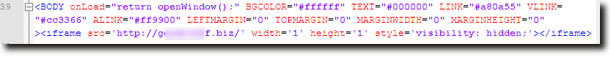
The modus operandi of the attackers was that they inserted a hidden iframe just after the body tag and this frame loads a series of malware on the computers of the unsuspecting customers of the bank, from 3 urls, as shown below.
Two of the URLs are now down but the third one contains an obfuscated JavaScript that uses exploits to download and run a file called 'loader.exe'. This file is a small downloader which downloads additional files which are different password stealing trojans, additional downloaders etc.
This collected data was then uploaded to a FTP server in Russia.
One interesting fact is that Trojan.Netview is specifically searching for quarantine folders of antivirus programs. It is no surprise that this particular person had over a hundred items located in their quarantine folder:

Actually in this case bank is also a victim, but the bank and its customers both are targeted collectively by the attackers. The bank can be sued by its customers for not practicing Due care and diligence in the court of law. But here in india the IT crime laws are not known to many.It was said that bank just migrated to IIS 6 probably the attackers used a 0- day to compromise the banks webserver
In this case instead of defacing the websites that the attackers usually do, they tried a different approach, they were successful in installing the malware in the millions of bank's net banking customers, and they used the malware(list given below) .
It is not known that for how many days the banks website remained compromised, it was just discovered a few hours ago, many of the passwords and personal information of the banks website has already reached the attackers.
Its high time that we get serious about the threats of the internet and start taking security seriously.
Some of the malware that were seen are:
Email-Worm.Win32.Agent.l
Rootkit.Win32.Agent.dw
Rootkit.Win32.Agent.ey
Trojan-Downloader.Win32.Agent.cnh
Trojan-Downloader.Win32.Small.ddy
Trojan-Proxy.Win32.Agent.nu
Trojan-Proxy.Win32.Wopla.ag
Trojan.Win32.Agent.awz
Trojan-Proxy.Win32.Xorpix.Fam
Trojan-Downloader.Win32.Agent.ceo
Trojan-Downloader.Win32.Tibs.mt
Trojan-Downloader.Win32.Agent.boy
Trojan-Proxy.Win32.Wopla.ah
Trojan-Proxy.Win32.Wopla.ag
Rootkit.Win32.Agent.ea
Trojan.Pandex
Goldun.Fam
Backdoor.Rustock
Trojan.SpamThru
Trojan.Win32.Agent.alt
Trojan.Srizbi
Trojan.Win32.Agent.awz
Email-Worm.Win32.Agent.q
Trojan-Proxy.Win32.Agent.RRbot
Trojan-Proxy.Win32.Cimuz.G
TSPY_AGENT.AAVG (Trend Micro)
Trojan.Netview
Due to this compromise millions of Customers of the banks website were left in the hands of attackers from Russia, who managed to install a number of Trojans and root kits in the computers of the bank's innocent customers, who may be using the net banking facility.
The modus operandi of the attackers was that they inserted a hidden iframe just after the body tag and this frame loads a series of malware on the computers of the unsuspecting customers of the bank, from 3 urls, as shown below.
Two of the URLs are now down but the third one contains an obfuscated JavaScript that uses exploits to download and run a file called 'loader.exe'. This file is a small downloader which downloads additional files which are different password stealing trojans, additional downloaders etc.

This collected data was then uploaded to a FTP server in Russia.
One interesting fact is that Trojan.Netview is specifically searching for quarantine folders of antivirus programs. It is no surprise that this particular person had over a hundred items located in their quarantine folder:

The following code can be clearly seen on the site:
Actually in this case bank is also a victim, but the bank and its customers both are targeted collectively by the attackers. The bank can be sued by its customers for not practicing Due care and diligence in the court of law. But here in india the IT crime laws are not known to many.It was said that bank just migrated to IIS 6 probably the attackers used a 0- day to compromise the banks webserver
In this case instead of defacing the websites that the attackers usually do, they tried a different approach, they were successful in installing the malware in the millions of bank's net banking customers, and they used the malware(list given below) .
It is not known that for how many days the banks website remained compromised, it was just discovered a few hours ago, many of the passwords and personal information of the banks website has already reached the attackers.
Its high time that we get serious about the threats of the internet and start taking security seriously.
Some of the malware that were seen are:
Email-Worm.Win32.Agent.l
Rootkit.Win32.Agent.dw
Rootkit.Win32.Agent.ey
Trojan-Downloader.Win32.Agent.cnh
Trojan-Downloader.Win32.Small.ddy
Trojan-Proxy.Win32.Agent.nu
Trojan-Proxy.Win32.Wopla.ag
Trojan.Win32.Agent.awz
Trojan-Proxy.Win32.Xorpix.Fam
Trojan-Downloader.Win32.Agent.ceo
Trojan-Downloader.Win32.Tibs.mt
Trojan-Downloader.Win32.Agent.boy
Trojan-Proxy.Win32.Wopla.ah
Trojan-Proxy.Win32.Wopla.ag
Rootkit.Win32.Agent.ea
Trojan.Pandex
Goldun.Fam
Backdoor.Rustock
Trojan.SpamThru
Trojan.Win32.Agent.alt
Trojan.Srizbi
Trojan.Win32.Agent.awz
Email-Worm.Win32.Agent.q
Trojan-Proxy.Win32.Agent.RRbot
Trojan-Proxy.Win32.Cimuz.G
TSPY_AGENT.AAVG (Trend Micro)
Trojan.Netview
Update: The malicious iframe has been removed from the front page and it's now safe to visit the site again.
This video shows the attack on any banks user using unpatched IE or mozilla.

No comments:
Post a Comment