|
For example, consider the theft of credit cards numbers. There is an unimaginable number of documented cases showing how stolen credit cards are used by cyber criminals to “go shopping” online or to run businesses where such cards are sold to third parties for a ridiculous price... but that’s not all.
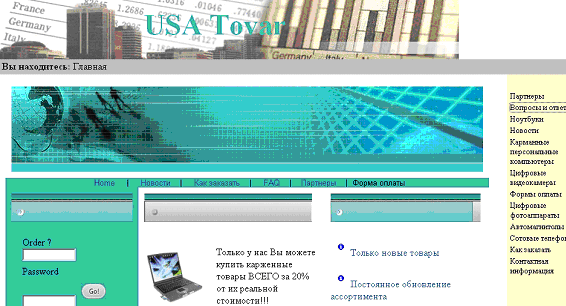
Indeed, Panda Software ‘s blog reported the news about a Russian Website selling Technological products that are openly said to have been bought using stolen and Cloned credit cards. As you can see in the image below, the Russian text says that the website offers laptops, cell phones and other items for 20% of their real value.
The reason for a similar discount can be found visiting the FAQ section of the website, where the question “How can you offer such good prices?” is answered with the statement: "It’s very simple. We buy these products in Western countries with stolen credit cards. You don’t run any risk when purchasing these products." …Welcome frankness! In such website there is also a “Partner Section”, inviting web administrators to join the business: “partners” would be given a code they should include on their website. This simple operation would make them get 25% of the money coming from they website.So this time beware before using the credit cards!! source:zone-h.com |
Saturday, July 28, 2007
Russian Website selling laptops, PDA's at throwaway prices
Friday, July 27, 2007
iPhone: NSA iSnoop Device?



In a white paper, according to the blog, the Russians indicate a possible “debug feature or a built-in backdoor module for some governmental structures,” i.e., the National Security Agency, the lead governmental structure responsible for violating en masse the constitutional rights of Americans.
Of course, it helps that “Apple has chosen AT&T, the best and most popular carrier in the US with over 62 million subscribers, to be Apple’s exclusive carrier partner for iPhone in the United States,” as the AT&T website boasts. As we know, the telecom leviathan illegally collaborated with the NSA to break the law.
“AT&T violated the law, and the rights of its customers, by allowing and assisting with the illegal wiretapping and data-mining. The government’s spying program on ordinary Americans would not be possible without AT&T collaborating in violating your privacy,” explains an Electronic Frontier Foundation FAQ. “EFF alleges that under the NSA domestic spying program, major telecommunications companies—and AT&T specifically—gave the NSA direct access to their vast databases of communications records, including information about whom their customers have phoned or emailed with in the past. EFF alleges that AT&T, in addition to allowing the NSA direct access to the phone and Internet communications passing over its network, and gave the government unfettered access to its over 300 terabyte ‘Daytona’ database of caller information—one of the largest databases in the world.”
“The essential hardware elements of a (Total Information Awareness)-type spy program are being surreptitiously slipped into ‘real world’ telecommunications offices,” Wired News reported former AT&T technician Mark Klein as writing. According to Klein and a report published by the New York Times, the NSA-AT&T “Orwellian project… is vastly bigger” than previously figured “and was directly authorized by President Bush, as he himself has now admitted, in flagrant violation of specific statutes and constitutional protections for civil liberties.” In the meantime, Bush has signed a number of executive orders essentially granting himself the power of a Roman Magister Populi, a dictatorial master over the commoners.
Considering all of this, it makes perfect sense for the Apple iPhone to double as an NSA iSnoop device.
“Last year, it was discovered that AT&T has been secretly spying on Americans for the government,” notes Adam Frucci for the Gizmodo blog. “Maybe it still is. Then, just recently, it announced that it planned to spy on Internet surfers yet again, looking for pirated media files, presumably to the delight of the RIAA and MPAA. If you don’t want to get spied on and want to switch ISPs, guess what? Depending on where you live, you might not have any other options. And if AT&T snoops on all data passing through its network, most US Internet users will be affected, not just AT&T customers. It runs a significant amount of the backbone infrastructure of the Internet, leaving little traffic outside its grasp.”
But never mind. Apple’s iPhone is so cool and trendy a lot of buyers and potential buyers will shrug off the fact the device is—if the Russian hackers who reverse engineered the gadget are correct—a custom-made snoop device that routes your personal data right to an NSA Cray super computer.
source: http://kurtnimmo.com/?p=931
Thursday, July 26, 2007
IE7 Local Software Enumeration
by Billy (BK) Rios – Billy dot Rios -at- gmail
Using the Resource URI, it is possible to set the img.src attribute to a resource within an executable or dll on the users local file system. Many executables (and some dlls) have bitmaps (and other images) embedded into the executable. These images can be loaded into an image object by setting the "src" property equal to the resource inside of an executable or dll on the user’s local file system. Loading of resources on the local file system is possible, even if the user is running IE with the highest security settings and has scripting disabled. The following HTML code demonstrates a simple way to enumerate software on a users local file system.
An attacker could initiate enumeration through XSS or by URL redirection. Attackers could scan a users file system for software with known vulnerabilities or an unscrupulous vendor could scan a users machine to determine whether the user has a competitors software, software related to a health condition, or other sensitive software installed creating a privacy risk for some users....
HERE's the demonstration
 The Cyber Criminals are here guys, and they are resorting to a number of ways to make money on the internet, here comes a classic case of cloned and stolen credit cards, a Russian website is selling products bought from credits cards that were stolen or cloned in USA!!
The Cyber Criminals are here guys, and they are resorting to a number of ways to make money on the internet, here comes a classic case of cloned and stolen credit cards, a Russian website is selling products bought from credits cards that were stolen or cloned in USA!!