Sunday, December 23, 2007
Saturday, September 1, 2007
Bank Of India Site Hacked and Serving Malware
Due to this compromise millions of Customers of the banks website were left in the hands of attackers from Russia, who managed to install a number of Trojans and root kits in the computers of the bank's innocent customers, who may be using the net banking facility.
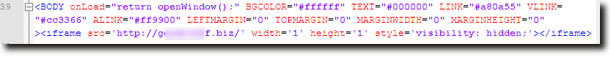
The modus operandi of the attackers was that they inserted a hidden iframe just after the body tag and this frame loads a series of malware on the computers of the unsuspecting customers of the bank, from 3 urls, as shown below.
Two of the URLs are now down but the third one contains an obfuscated JavaScript that uses exploits to download and run a file called 'loader.exe'. This file is a small downloader which downloads additional files which are different password stealing trojans, additional downloaders etc.
This collected data was then uploaded to a FTP server in Russia.
One interesting fact is that Trojan.Netview is specifically searching for quarantine folders of antivirus programs. It is no surprise that this particular person had over a hundred items located in their quarantine folder:

Actually in this case bank is also a victim, but the bank and its customers both are targeted collectively by the attackers. The bank can be sued by its customers for not practicing Due care and diligence in the court of law. But here in india the IT crime laws are not known to many.It was said that bank just migrated to IIS 6 probably the attackers used a 0- day to compromise the banks webserver
In this case instead of defacing the websites that the attackers usually do, they tried a different approach, they were successful in installing the malware in the millions of bank's net banking customers, and they used the malware(list given below) .
It is not known that for how many days the banks website remained compromised, it was just discovered a few hours ago, many of the passwords and personal information of the banks website has already reached the attackers.
Its high time that we get serious about the threats of the internet and start taking security seriously.
Some of the malware that were seen are:
Email-Worm.Win32.Agent.l
Rootkit.Win32.Agent.dw
Rootkit.Win32.Agent.ey
Trojan-Downloader.Win32.Agent.cnh
Trojan-Downloader.Win32.Small.ddy
Trojan-Proxy.Win32.Agent.nu
Trojan-Proxy.Win32.Wopla.ag
Trojan.Win32.Agent.awz
Trojan-Proxy.Win32.Xorpix.Fam
Trojan-Downloader.Win32.Agent.ceo
Trojan-Downloader.Win32.Tibs.mt
Trojan-Downloader.Win32.Agent.boy
Trojan-Proxy.Win32.Wopla.ah
Trojan-Proxy.Win32.Wopla.ag
Rootkit.Win32.Agent.ea
Trojan.Pandex
Goldun.Fam
Backdoor.Rustock
Trojan.SpamThru
Trojan.Win32.Agent.alt
Trojan.Srizbi
Trojan.Win32.Agent.awz
Email-Worm.Win32.Agent.q
Trojan-Proxy.Win32.Agent.RRbot
Trojan-Proxy.Win32.Cimuz.G
TSPY_AGENT.AAVG (Trend Micro)
Trojan.Netview
Update: The malicious iframe has been removed from the front page and it's now safe to visit the site again.
This video shows the attack on any banks user using unpatched IE or mozilla.
Wednesday, August 15, 2007
Saturday, July 28, 2007
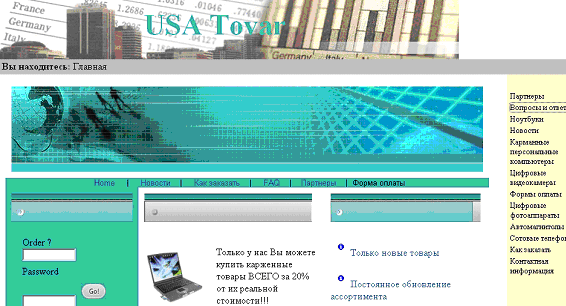
Russian Website selling laptops, PDA's at throwaway prices
|
For example, consider the theft of credit cards numbers. There is an unimaginable number of documented cases showing how stolen credit cards are used by cyber criminals to “go shopping” online or to run businesses where such cards are sold to third parties for a ridiculous price... but that’s not all.
Indeed, Panda Software ‘s blog reported the news about a Russian Website selling Technological products that are openly said to have been bought using stolen and Cloned credit cards. As you can see in the image below, the Russian text says that the website offers laptops, cell phones and other items for 20% of their real value.
The reason for a similar discount can be found visiting the FAQ section of the website, where the question “How can you offer such good prices?” is answered with the statement: "It’s very simple. We buy these products in Western countries with stolen credit cards. You don’t run any risk when purchasing these products." …Welcome frankness! In such website there is also a “Partner Section”, inviting web administrators to join the business: “partners” would be given a code they should include on their website. This simple operation would make them get 25% of the money coming from they website.So this time beware before using the credit cards!! source:zone-h.com |
Friday, July 27, 2007
iPhone: NSA iSnoop Device?



In a white paper, according to the blog, the Russians indicate a possible “debug feature or a built-in backdoor module for some governmental structures,” i.e., the National Security Agency, the lead governmental structure responsible for violating en masse the constitutional rights of Americans.
Of course, it helps that “Apple has chosen AT&T, the best and most popular carrier in the US with over 62 million subscribers, to be Apple’s exclusive carrier partner for iPhone in the United States,” as the AT&T website boasts. As we know, the telecom leviathan illegally collaborated with the NSA to break the law.
“AT&T violated the law, and the rights of its customers, by allowing and assisting with the illegal wiretapping and data-mining. The government’s spying program on ordinary Americans would not be possible without AT&T collaborating in violating your privacy,” explains an Electronic Frontier Foundation FAQ. “EFF alleges that under the NSA domestic spying program, major telecommunications companies—and AT&T specifically—gave the NSA direct access to their vast databases of communications records, including information about whom their customers have phoned or emailed with in the past. EFF alleges that AT&T, in addition to allowing the NSA direct access to the phone and Internet communications passing over its network, and gave the government unfettered access to its over 300 terabyte ‘Daytona’ database of caller information—one of the largest databases in the world.”
“The essential hardware elements of a (Total Information Awareness)-type spy program are being surreptitiously slipped into ‘real world’ telecommunications offices,” Wired News reported former AT&T technician Mark Klein as writing. According to Klein and a report published by the New York Times, the NSA-AT&T “Orwellian project… is vastly bigger” than previously figured “and was directly authorized by President Bush, as he himself has now admitted, in flagrant violation of specific statutes and constitutional protections for civil liberties.” In the meantime, Bush has signed a number of executive orders essentially granting himself the power of a Roman Magister Populi, a dictatorial master over the commoners.
Considering all of this, it makes perfect sense for the Apple iPhone to double as an NSA iSnoop device.
“Last year, it was discovered that AT&T has been secretly spying on Americans for the government,” notes Adam Frucci for the Gizmodo blog. “Maybe it still is. Then, just recently, it announced that it planned to spy on Internet surfers yet again, looking for pirated media files, presumably to the delight of the RIAA and MPAA. If you don’t want to get spied on and want to switch ISPs, guess what? Depending on where you live, you might not have any other options. And if AT&T snoops on all data passing through its network, most US Internet users will be affected, not just AT&T customers. It runs a significant amount of the backbone infrastructure of the Internet, leaving little traffic outside its grasp.”
But never mind. Apple’s iPhone is so cool and trendy a lot of buyers and potential buyers will shrug off the fact the device is—if the Russian hackers who reverse engineered the gadget are correct—a custom-made snoop device that routes your personal data right to an NSA Cray super computer.
source: http://kurtnimmo.com/?p=931
Thursday, July 26, 2007
IE7 Local Software Enumeration
by Billy (BK) Rios – Billy dot Rios -at- gmail
Using the Resource URI, it is possible to set the img.src attribute to a resource within an executable or dll on the users local file system. Many executables (and some dlls) have bitmaps (and other images) embedded into the executable. These images can be loaded into an image object by setting the "src" property equal to the resource inside of an executable or dll on the user’s local file system. Loading of resources on the local file system is possible, even if the user is running IE with the highest security settings and has scripting disabled. The following HTML code demonstrates a simple way to enumerate software on a users local file system.
An attacker could initiate enumeration through XSS or by URL redirection. Attackers could scan a users file system for software with known vulnerabilities or an unscrupulous vendor could scan a users machine to determine whether the user has a competitors software, software related to a health condition, or other sensitive software installed creating a privacy risk for some users....
HERE's the demonstration
The Following Software was Discovered on your Computer:
Wednesday, June 27, 2007
Backdoors in CISCO devices and routers
Could Your VoIP Phone Be Tapped?
FBI: putting a backdoor in every router soon?
How nice. The FCC wants "a "back door" be built into all Internet-communications hardware and software to provide access for law enforcement agencies".
The FBI wants all future routing equipment manufactured to include backdoors for law enforcement. Like in CALEA, such back doors require no warrant to activate, and hence can be secretly enabled at will.
And there are reports that CISCO is already doing it with its routing equiptments.
So may be we can used the routers based on linux.... heres the link
http://www.imagestream.com/index_800.html
These companies will be given 18 months time to comply and moreover the cost of this will be passed on to the consumers, we are paying for being able to spied upon us!!
EFF and a coalition of public interest, industry, and academic groups filed suit in 2005 challenging the Federal Communications Commission's (FCC) unjustified expansion of the Communications Assistance for Law Enforcement Act (CALEA). By forcing broadband Internet and interconnected voice over Internet Protocol (VoIP) services to become wiretap-friendly, the FCC ignored CALEA's plain language and threatened privacy, security, and innovation.
The FCC's final rule, issued on August 5, 2005, would extend CALEA to all Internet-based communications, according to EFF Chairman Brad Templeton, who spoke at Emerging Telephony Conference here, sponsored by O'Reilly Media. Once the FCC issues a final rule, vendors have 18 months to comply with it.
So guys we dont have any security over internet, we hav US Govt, NSA spying over it all the time.BEWARE..!!
The story starts long ago but for our purpose we can pickup the thread in 1998. Lets us just consider The United States: US companies wanting to export Network related equipment and software were restricted before that time by USA laws to only being able to export low (easily breakable) encryption products. Where as customers abroad demanded high encryption products. US government (read here National Security Agency i.e. NSA – the spy agency for USA) required that to be able to export high encryption products the product makers should either give a key (to be able to read all the encrypted information) to them or provide alternate means to be able to read this information. In a landmark deal which was agreed by 13 major manufacturers of hardware/software (these include: Ascend, Bay Networks, Cisco Systems, 3Com, Hewlett-Packard Company, Intel, Microsoft, Netscape Communications, Network Associates, Novell, RedCreek Communications, Secure Computing and Sun Microsystems) agreed to build in a private doorbell in the products they made which on a command from NSA – so to say, flicks a “network control switch”, that makes the product surreptitiously record everything you type or do online before it is encrypted (e.g. a Cisco router software begins to surreptitiously record everything you type or do online). That information is bundled into a file that can be sent or picked up by NSA. Please note this was solution arrived at in mid-1998. In last four years we don’t know what other means have been developed to collect the information at will by NSA.



 The Cyber Criminals are here guys, and they are resorting to a number of ways to make money on the internet, here comes a classic case of cloned and stolen credit cards, a Russian website is selling products bought from credits cards that were stolen or cloned in USA!!
The Cyber Criminals are here guys, and they are resorting to a number of ways to make money on the internet, here comes a classic case of cloned and stolen credit cards, a Russian website is selling products bought from credits cards that were stolen or cloned in USA!!